Automatically Refresh Entra ID Group Memberships in Azure DevOps
Summary
Azure DevOps becomes exceptionally powerful when integrated with Microsoft Entra ID. However, one noticable challenge arises in the delay of updating group memberships within Azure DevOps as those updates are neither transparent nor of immediate effect. Waiting times get even more challenging when Azure DevOps permissions are used in conjunction with Privileged Identity Management. To alleviate the administrative burden, an API call can be used to enforce the synchronization cycle programmatically.
Solution
From Web to CLI
Identifying the required API Call
As the Azure DevOps internal APIs are lacking comprehensive documentation, we start by reviewing the actions required on https://dev.azure.com to find a way of automating the required procedure. This methodology often helps getting behind the covers of Web Frontends. However, for more complex setups, tools like Postman API Platform or Swagger may be a better fit.
Note: For this, you have to have Organization Administrator permissions on Azure DevOps. To circumvent this requirement, I spawned a Microsoft 365 Developer Tenant at Set up a Microsoft 365 developer sandbox subscription | Microsoft Learn
Note: For reference on supported parameters after figuring out the required API endpoint, please refer to this blog.
When logged to Azure DevOps, switch to Organization Settings -> Users -> Group Rules.
Here, you can trigger the Group Membership Update by clicking Re-evaluate Rules after opening the Developer Console and switch to the Network tab.
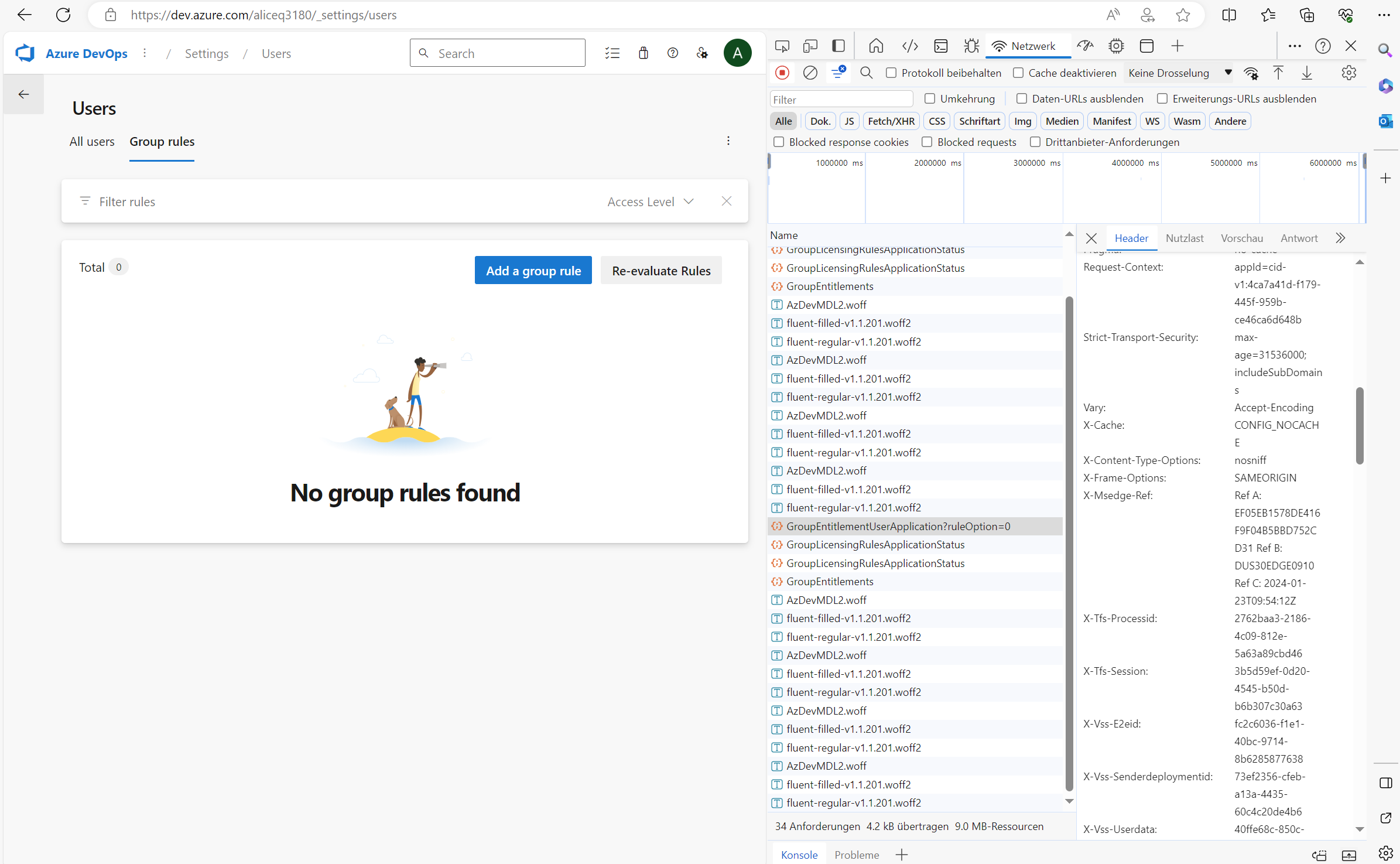
After invoking the action from the GUI, the required parameters can be taken from the spawned GroupEntitlementUserApplication Post Command.
Running the Operation locally
Initially, setup Azure DevOps CLI in your shell of choice by following the instructions at Microsoft Learn.
Now, you can use the invoke sub-command to trigger the identified action locally and review the output:
az devops invoke `
--area MEMInternal `
--resource GroupEntitlementUserApplication `
--api-version 6.0-preview `
--http-method post
From CLI to Pipeline
Finally, to automate the operation further and prevent users from requiring Organization Administrator permissions in day-to-day operations, you can assemble a pipeline and run it from Azure DevOps. For that to work, you have to have a PAT holding the required permissions and store it as a Pipeline Variable (preferably from an Azure KeyVault).
Your pipeline will probably look similar to this:
trigger: none
pool: ubuntu-latest
variables:
- group: <your variable group containing the PAT variable and organization>
steps:
- script: | `
az extension add --name azure-devops `
echo $AZURE_DEVOPS_EXT_PAT | az devops login --org $AZDO_ORG_SERVICE_URL `
az devops invoke --area MEMInternal --resource GroupEntitlementUserApplication --api-version 6.0-preview --http-method post --verbose
displayName: 'Refresh Azure DevOps Group Memberships'
env:
AZURE_DEVOPS_EXT_PAT: $(<Azure DevOps Variable name from Variable Group above>)
AZDO_ORG_SERVICE_URL: $(System.CollectionUri)
Running the pipeline, your output will probably look familiar to the screenshot above.
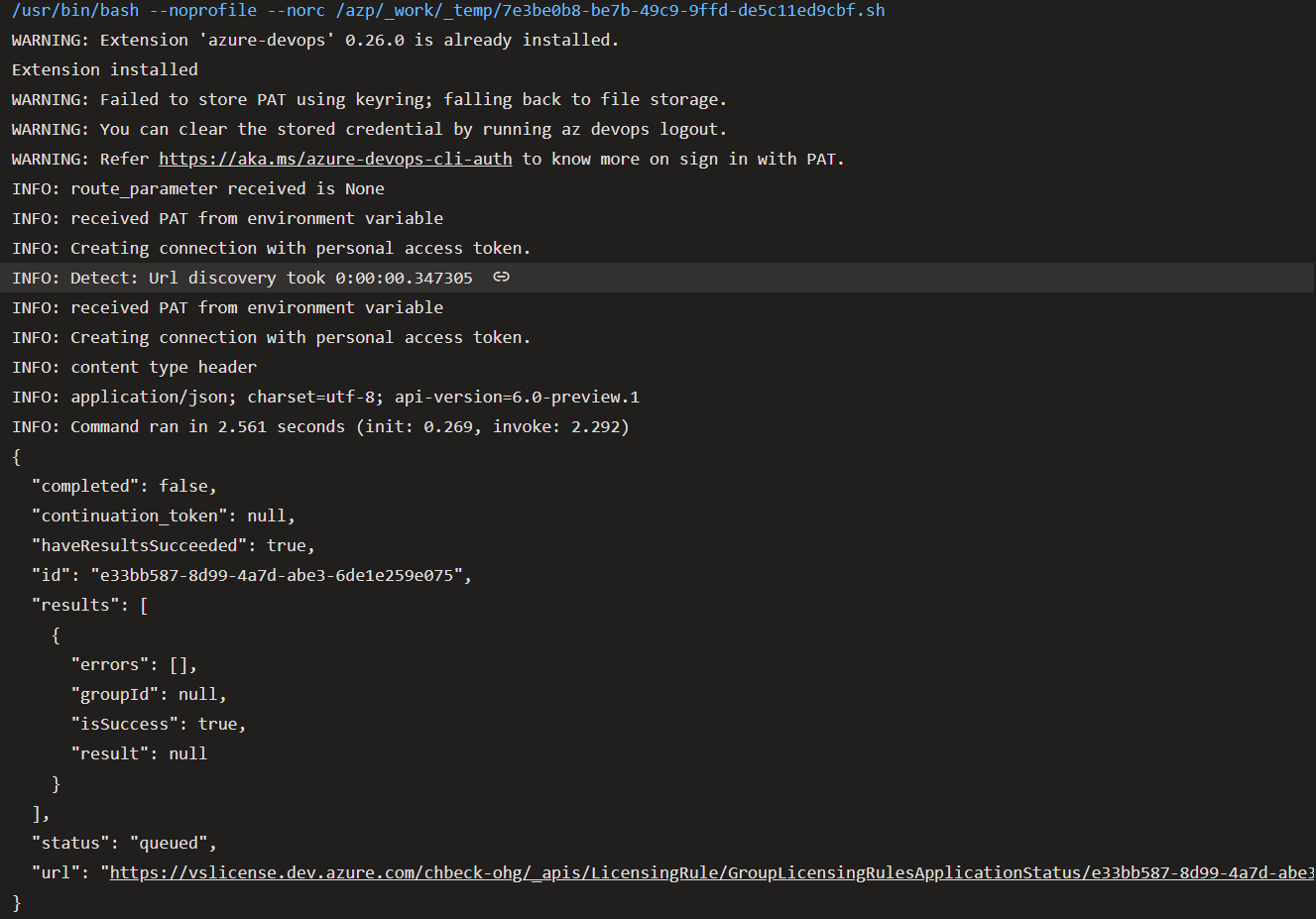
As the command is executed asynchronously, wait for up to a minute to check for the updated group memberships in Azure DevOps.
For use-cases like PIM, it is possible to trigger the pipeline from a webhook that is send on a PIM event, but we will save that for a later post.
Cheers!